blog.mironov.live
Browser extensions could be spying on you, and that is not their fault
February 27, 2019
Ad blockers, VPN services, password managers, typo correctors, and other browser extensions have full access to all your personal data on all pages that you visit including password, credit cards, and private photos.
Animation by Dasha Mironova
I’ll not claim that any particular extension collects such information but I’ll show you why it is possible and what you can do about that. However, there were numerous privacy scandals with extensions.
What the heck I’m talking about?
I developed a Google Chrome extension that was eventually used by 14000 users. I received shady proposals to monetize my extension once a month.
Monetizing, in this case, is just another way to say fraud because those people suggest showing users unwanted advertisements instead of images or legitimate banners, and use other not quite ethical methods of earning money.
For example, you can use one of the so-called “free” VPN services. It can earn money to cover servers costs by replacing Amazon links to affiliated ones, all Google Adwords blocks with third-party banners, or simply send to its servers everything that you type into email and password fields. No one ever read privacy policies anyway, right? Besides that, such extensions can simply lie there.
Why is it possible?
Browser developers are very smart people. They allowed the whole new ecosystems to emerge and grow on top of browsers. Extensions add missing functionality to browsers and I recommend using them. The main problem is lying in the access control that extensions request on installation. I will give examples for Google Chrome but Firefox, Opera, and many smaller browsers use the same extensions format so the problems are the same.
Full access problem
Everyone who installed an extension saw the following modal:
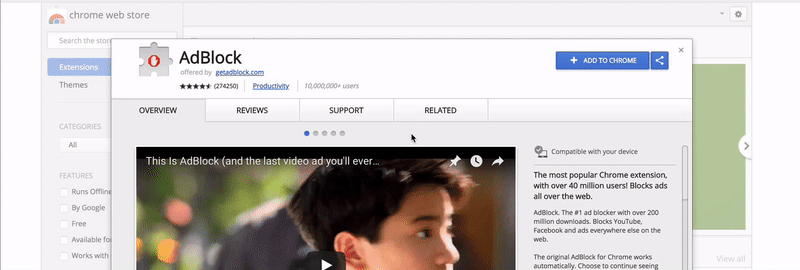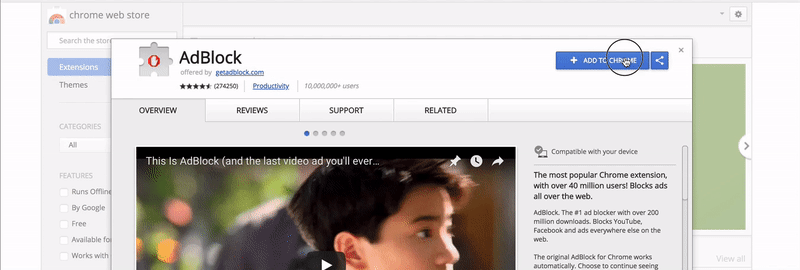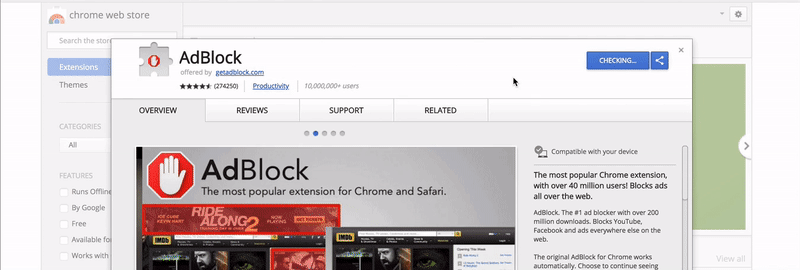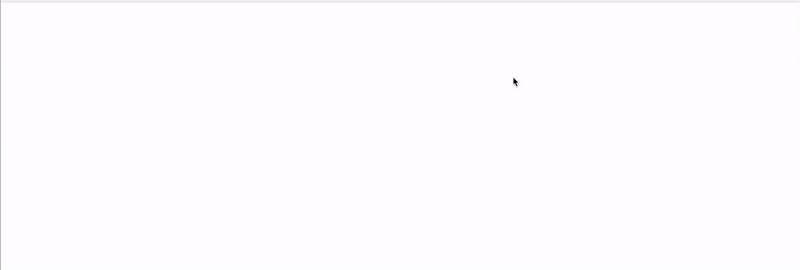
Have you noticed that? The extension just asked full access to read and modify all data on all pages that you visit. I allowed it with a single click. UI/UX professionals can confirm that the modal looks like a regular modal to confirm action “Are you sure you want to install the extension?“. Even if you read the notice carefully, it’s kind of hard to understand what the phrase means exactly.
The true meaning is that the extension, in fact, receives permission to execute any code on any page that you visit. This can be happening in the background without your consent. Moreover, the extension can perform HTTP requests, again, in the background, so even Web Inspector won’t show them.
Extensions have a way to specify on which sites they will work but there is no way to request access to do only particular actions. For example, you can’t request permission to:
- add code to sites AND NOTHING ELSE (dictionaries, readers)
- fill form inputs AND NOTHING ELSE (password managers)
- remove parts of the HTML code AND NOTHING ELSE (ad blockers)
This is the main problem. If extension needs to do almost anything with page content, it has no other choice but to request the “read and modify all data” permission. It is a mystery to me why browsers don’t implement more fine-grained access control.
Complementary access problem
If an extension needs more permissions in an update, it won’t be updated until the user explicitly allows it by clicking on the exclamation mark on the toolbar:
Update warning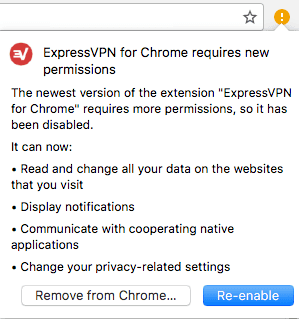
It is not unusual to encounter recommendations for extensions developers to request full access from the beginning, just in case. That’s why there are so many extensions in the store with full access.
So, back to monetization. Extensions developers are constantly bombarded with emails similar to the following one:
Email 1 Email 2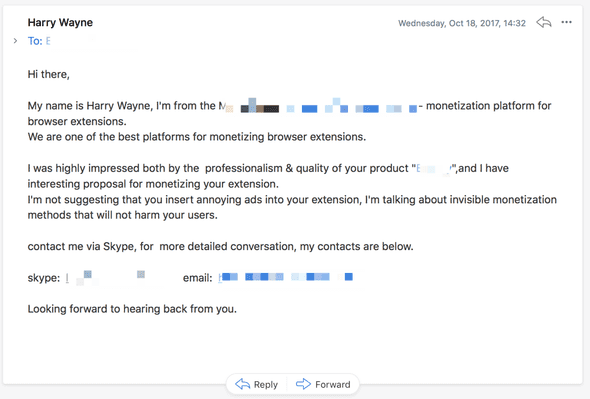
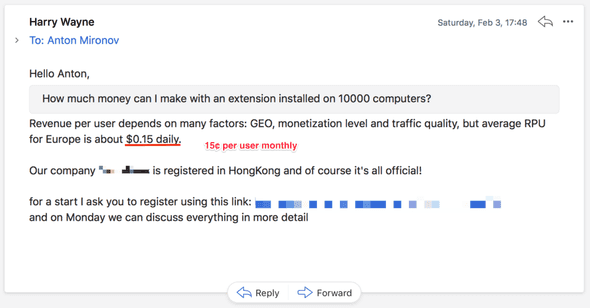
Now imagine that you are an indie developer. You do want to make $1000 passively on your extension, don’t you?
Proposed ways to monetize extensions:
- fill empty spaces in the sidebar with banners
- replace images with banners
- insert banners at the bottom of the page
- popup banners
- insert promotional posts on facebook
- insert promotional search result in google
- video preroll
- replace links to Amazon with referral links
- insert middle-page between click and the actual page load
You might ask: “wait… extension stores have moderation and review process, why do they allow that?“.
Moderators approve extensions on initial publication and before each update. Google Chrome, apparently, approves extensions automatically because that approval takes only a couple of minutes. It is not technically possible to determine whether an extension contains malicious code or not. The code of the extension is usually minified, and an extension can download additional code from the internet after installation, and execute it without any approval. I don’t even say anything about non-trivial key loggers and other shady techniques .
Non-obvious interface problem
I have a feeling that Google is deliberately hiding the problem. Look at the list of installed extensions in Google Chrome:
Extensions list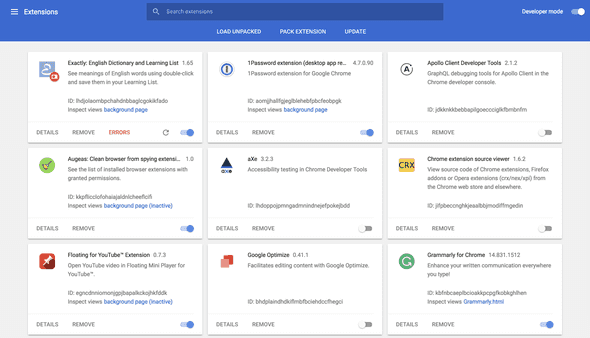
You can’t determine which of installed extensions have full access. Since most of the extensions were installed without carefully looking into requested permissions, there is a good chance that you don’t remember what exactly some of your extensions doing.
First two problems should be addressed by browsers developers but the third problem could be solved on our own. I open sourced very basic extension that displays a list of installed extensions along with human-readable permissions that they requested.
Better extensions list
You can install it by following the link: Augeas: Clean browser from spying extensions - Chrome Web Store
Why another extension?
It is possible to get a list of installed extensions only when chrome.management permission is granted. It is not possible to do that from websites. I recommend to go through all installed extensions and uninstall suspicious ones or those for whom you don’t trust your credit card.
Lastly, delete Augeas itself and be careful when installing new extensions.

Written by Anton Mironov.
Follow on Twitter